Streamline PCI Compliance Efforts
Good on their own, but better together, vulnerability management and pen testing can greatly streamline your efforts to achieve PCI Compliance. Vulnerability management scans, identifies, prioritizes, and reports on security weaknesses while pen testing validates the exploitability an organization’s infrastructure weaknesses, showing exactly how a cyber attacker could use vulnerabilities to gain access to sensitive data.
Penetration Testing for PCI Compliance
Pen testing services and software are a great way to evaluate the security of networks, applications, endpoints, and users. Depending on your company’s security team, services are a good way to give them an additional hand and software is a great way to give them the security tools they need.
Core Impact Penetration Testing Software
Pen testers can use Core Impact to efficiently conduct penetration tests and solidify their security programs with strategic automation. A security team of any experience level can use this automation safely to guide them through critical standard testing and maximize their time with automated routines.
Penetration Testing Services
Fortra’s pen testing services provide you with a team of ethical professionals to test your security systems and report back with an objective, expert view of your security posture. These security experts can customize each test and expose potential attack paths. that may have been overlooked.
Vulnerability Management for PCI Compliance
Fully Managed PCI Scanning Services
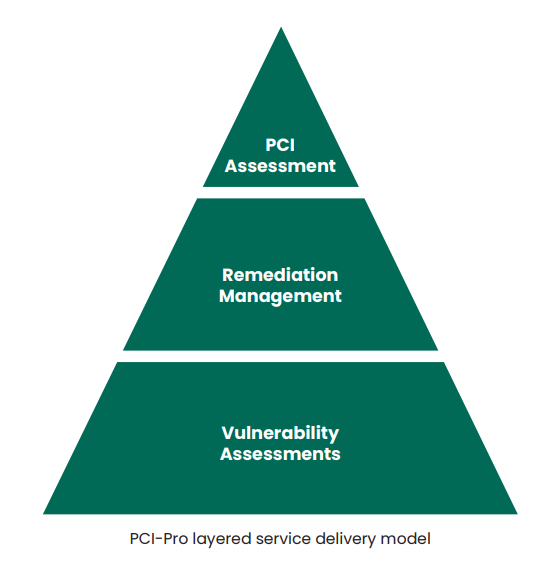
Unlike other vendors who promote a “fail until you pass” mindset to compliance, we use a stepping stone approach where compliance resides at the top of a three-tiered pyramid including comprehensive PCI network vulnerability scanning and remediation management.
- Tier 1 focuses on the foundation of comprehensive vulnerability.
- Tier 2 adds remediation management – addressing identified vulnerabilities in a systematic, efficient and cost-effective manner.
- Tier 3, focuses on leveraging results from Tier 1 and 2 to produce the reports necessary to achieve successful compliance with applicable PCI DSS requirements.
PCI Self-Service Scanning
We also offer self-service scans that your team can get up and scanning in minutes.
- Flexible, Simple Deployment
- Scalable Scanning
- Differential Reporting
Learn more here.
PCI Compliance: Past, Present, and Future
PCI compliance was initially designed to focus on payment card accounts, but it’s grown into a larger payment card data threat protection entity. Fast forward to today, payment card transactions, the data exchanged, and the payment information housed is covered by PCI Compliance regulations. It’s no longer singularly focused on the payment card, but the entire process, including data retention and transmission.
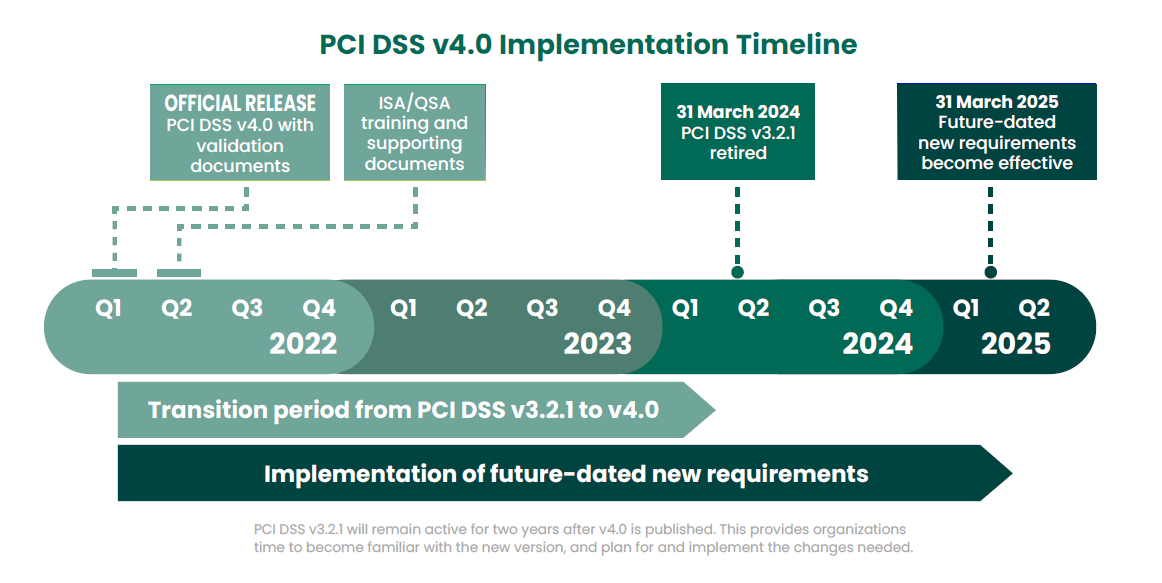
Organizations that must adhere to PCI compliance need to stay up to date with the requirement changes in PCI 4.0, including:
- Ensure they meet requirements for secure digital payments
- Foster security as a continuous dynamic process – not a one and done.
- Make validation procedures more robust
- Support any additional methodologies that achieve the target security goals
These new 4.0 requirements take into consideration that not all security approaches are the same, even if they are working toward the same goal. It allows for more customized methods when necessary to achieve PCI DSS requirements, empowering teams to choose the tools they want to work with to achieve the goals. For many security teams this means they can opt for powerful yet user-friendly solutions that streamline the PCI compliance process.
Powerful, User-Friendly PCI Compliance Tools
Core Impact Pen Testing Software Key Features:
- Intuitive automation
- Extensive and reliable library of certified exploits
- Multi-vector testing capabilities
- Teaming capabilities
- Tailored reporting
- Powerful integrations with other pen testing tools and more than 20 vulnerability scanners
- Robust safety features, including fully encrypted, self-destructing agents
- Monitors: Windows, Linux, Mac, Cloud, Databases, Web Services, network and software appliances, your critical data
Fortra Vulnerability Scanning and Management Key Features:
- Security GPA® security posture rating
- Insight peer comparison
- Network Map asset visualization
- Threat Rank exploitability context
- Connect API
- PCI ASV Certified 19 years
- PCI scanning and managed services available
Let Our Security Experts Help
Contact us and our cybersecurity professionals will help you find
the right solution for your PCI Compliance needs.